Recreating Bitcoin 6:Version 0.0.2 is Online!
Prologue #
Satoshi worked with Gilfoyle to complete the design of Bitcoin v0.0.2.
Important changes include:
1.Adding digital signature
2.Public key replacing username
3.Adding signature to the transaction model
4.Deleting the account model
The new update has made transacting ever freer!
Creating a Private Key #
Midway, inside the cafe. After a week of developing and testing, Bitcoin v0.0.2 was launched.
Satoshi went to Bob, “Hi Bob. Bitcoin has just updated to its latest version! If new customers want to join, they no longer need to register with me. They can create account themselves (that is, create address).”
“Fantastic! Anyone fancy a cup of coffee? And try out the new system!” Bob announced to the whole store.
“I’ll have a go. I was just about to get a cappuccino as well,” Alice came around the counter.
Alice took out his phone and entered bitcoin.org on the browser. A different-looking website showed up.
“It looks different!” Alice said, surprised (see graph below).
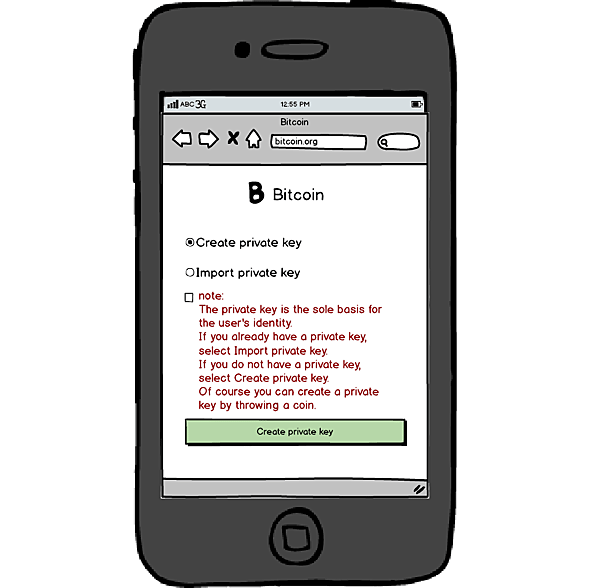
New login page of the new version
“The first thing to do here is to create a private key,” Satoshi said.
“What’s a private key?” Alice asked.
“You can take it as the password to your account. It’s a long password, which replaces the previous username and password altogether,” Satoshi explained.
“I see. Hm,” Alice seemed to have understood.
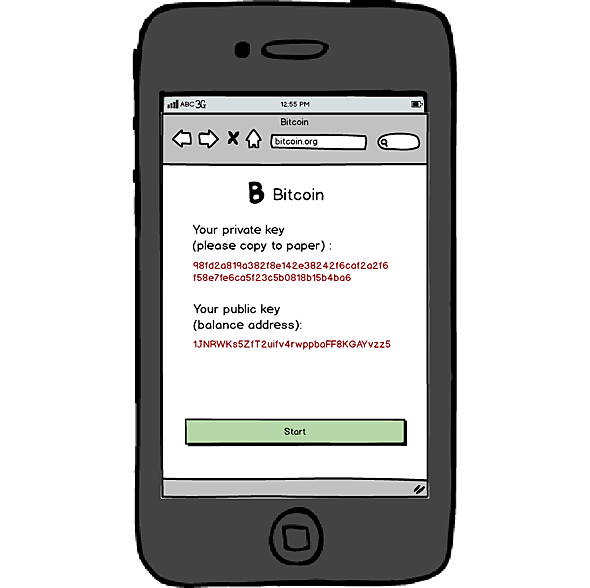
Alice chose to create private key, clicked the confirm button, and entered a new web page (see graph below).
Newly generated private key and public key
Alice wrote down the private as instructed, “What’s this public key then?”
“You can understand it as your recipient address. You use it to look up your balance. In fact, only the private key is known by yourself. Everyone can see your public key,” Satoshi said in a very fast pace, as if he tried to cram in a sentence as much information as possible.
Bob interjected as he was cleaning a cup, “this private key looks important. Where is it generated? The server side or the client side (browser is the client side)? Is it safe? How did you manage it? I learned some coding in the past. Maybe I can understand it.”
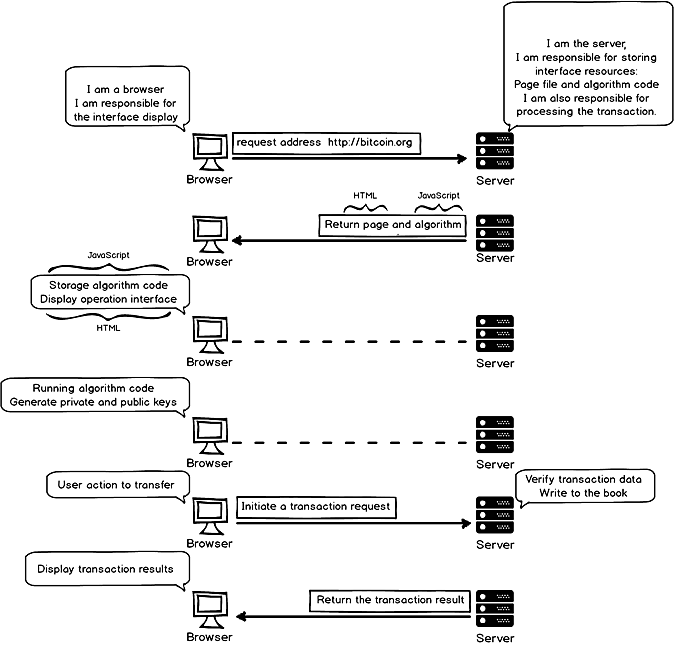
“It turns out you know some coding too,” Satoshi said. “Well, private key is generated on the client side, never to be transmitted in the network to prevented being hacked. If other people get their hands on it, you can lose all of your balance in seconds.”
He continued, “but the algorithm generating the private key is stored on the server side. When the browser visited bitcoin.org the first time, the server sent the algorithm code to the browser. When the user clicks the create private key button, the browser runs the algorithm code. This last process doesn’t interact with the server, so the private key won’t be transmitted in the network.” (see graph below)
Interactions between browser and server during generation of private key
“That sounds safe enough. I’m relieved to hear it,” Bob said.
“Actually, this design is not yet safe enough. Because the control over the algorithm is at the server’s end, if I want to commit malicious acts, I only need to change the algorithm code in the server and take control over the key-generating algorithm,” Satoshi added, with a contemplating face.
“But I believe you won’t do that,” Bob said.
“Humans are not reliable. With enough of an incentive, I can’t guarantee I won’t either,” Satoshi said.
He added, “but if you don’t mind some trouble, you can throw a coin to generate the private key and import it.”
Transactions #
“I trust you. Now I want to make a transaction. What’s your address Bob?” Alice asked.
“I will send it to you over text so you won’t need to manually enter it,” said Bob.
“Hold on Alice. Your newly created address currently has a balance of 0. I need to manually change the balance sheet to transfer your previous amount here,” Satoshi said.
Satoshi logged in the server and updated the data. Alice’s account was as good as before (see graph below).
Transacting to Bob’s public key
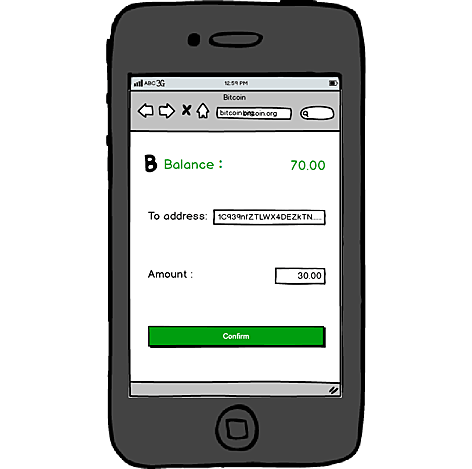
Bob turned on his phone and checked his balance (see graph below).
Bob’s balance page
“This is great! In this new system, now account registration is gone. The public key address protects user’s privacy. So how’s a transaction processed now?” Bob commented very happily.
“Right. Let’s start from when Alice clicked the transact button,” Satoshi started.
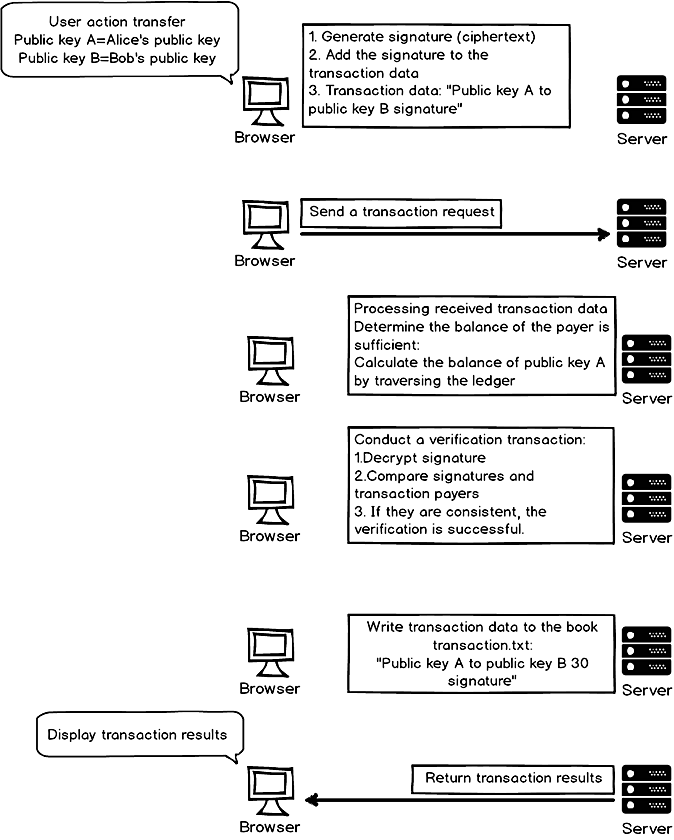
“First the browser generated transaction data, which was comprised of two parts: service data and signature. Service data was ‘Public Key A to Public Key B 30.’ Public Key A was Alice’s public key and Public Key B was Bob’s. Signature was generated by Alice’s private key encrypted Alice’s public key.”
“Then, the browser entered the transaction data into the message and sent a request to the server.”
“Server received the message and got the transaction data.”
“Server first needed to verify if the balance was sufficient: transaction.txt searched for records belonging to Public Key A and calculated the balance.”
“Server then proceeded to verify if the signature was valid: it used Public Key A to decrypt the signature and checked if the signature matched Public Key A. If it was a match then verification was a success.”
“Server entered the transaction data to the ledger and sent the result back to the browser.”
“Browser received the feedback and displayed the result on the web page.” (see graph below)
Interactions between browser and server during a transaction
Alice grabbed the coffee passed over by Bob. The first transaction in the new system had just been a success!
The new update had been successful. Satoshi felt very confident now with Gilfoyle collaboration.
But where there is coding, there’s bugs.
Epilogue #
This chapter revealed the whole scene behind the system’s operations.
But bugs still existed in the current design. We will see what it is in the next chapter.
Next chapter :Recreating Bitcoin 7:UTXO
CONTENTS #
Recreating Bitcoin:A Fictional Story of Why Bitcoin was Designed This Way
Part one : Transactions
Recreating Bitcoin 1:Start over with a Simple Web Transaction System
Recreating Bitcoin 2:First Version is Online!
Recreating Bitcoin 3:Getting Rid of the Account Model
Recreating Bitcoin 4:Digital Signature
Recreating Bitcoin 5:Public Key and Private Key
Recreating Bitcoin 6:Version 0.0.2 is Online!
Recreating Bitcoin 7:UTXO
Recreating Bitcoin 8:System Refactoring Based on UTXO
Recreating Bitcoin 9:Everything is Transaction
Recreating Bitcoin 10:Transaction Script
Part Two : Swarm System
Recreating Bitcoin 11:Swarm System (Part I)
Recreating Bitcoin 12:Swarm System (Part II)
Recreating Bitcoin 13:P2P Network
Recreating Bitcoin 14:Synchronizing Transactions
Recreating Bitcoin 15:Synchronizing Ledger
Recreating Bitcoin 16:Block chain
Recreating Bitcoin 17:Network Flexibility
Recreating Bitcoin 18:Proof of Work (Part I)
Recreating Bitcoin 19:Proof of Work (Part II)
Recreating Bitcoin 20:The Reorganization and Division of
Forking
Complete book selling at Amazon( > US > UK > CA > JP > DE > FR > ES > IT) #
BSV Donate:
1Djc4TdVBi8urzmSXKHwg8cpEAYKcRQxgY
©2019 - Recreating.org all rights reserved